Traffic Spike Evidence: Pattern of Institutional Monitoring Across Arms Export Campaigns
Editorial analysis documenting traffic spike pattern across three advocacy campaigns (Hanwha submarine, ADEX arms expo, APEC). Traffic spikes 7-10x normal baseline demonstrate strong timing correlation with government/defense industry outreach, suggesting documentation reaches institutional decision-makers.
October 30, 2025
Methodology Note: This analysis is based on timestamped analytics data, email campaign records, and cross-referenced documentation. We use Fathom Analytics (privacy-focused), which does not track source IP addresses. Traffic spike magnitudes and timing correlations are objectively verifiable, but we cannot establish definitive causation—only strong correlation between outreach timing and traffic patterns. Geographic data shows August 29 traffic primarily from Singapore (possible VPN exit node), while ADEX and APEC campaigns showed mixed countries with partial overlap to recipient organizations' home countries. Our analysis interprets these correlations as likely institutional monitoring, but acknowledges evidentiary limitations inherent in privacy-respecting analytics.
Executive Summary
Over the past three months, our advocacy work targeting arms export accountability has triggered a consistent, measurable pattern of institutional monitoring. Three separate campaigns—spanning Canadian submarine procurement, Seoul's international arms exposition, and APEC summit censorship—each produced immediate traffic spikes of 7-10x our normal baseline (2-15 views/day) within 24-48 hours of institutional outreach.
This is not coincidence. This is evidence.
The Pattern:
- Campaign 1 (Aug 27): Hanwha submarine warning to Canadian government → 129 views (10x spike)
- Campaign 2 (Oct 22): ADEX arms expo email campaign (135 recipients) → 105 views (7-10x spike)
- Campaign 3 (Oct 29-30): APEC press outreach → 20+ visitors averaging 5 pages/visitor
The consistency of this pattern—across different advocacy targets, different platforms, different time periods—establishes that our documentation successfully reaches institutional decision-makers and triggers systematic monitoring responses. This is not organic readership. This is institutional surveillance.
Pattern Overview: Three Campaigns, One Response
| Campaign | Date | Platform | Target Audience | Traffic Spike | Baseline | Multiplier |
|---|---|---|---|---|---|---|
| Hanwha Submarine | Aug 27, 2025 | X.com + Blog | Canadian govt | 129 views (Aug 29) | 2-15/day | 10x |
| ADEX Arms Expo | Oct 22, 2025 | Email + Blog | 135 defense industry | 105 views | 2-15/day | 7-10x |
| APEC Censorship | Oct 29-30, 2025 | Press + Blog | Media, govts | 20+ visitors, 5 pages each | 2-15/day | Research behavior |
What this strongly suggests: Documentation reaches institutional actors. Timing correlation demonstrates strong correlation, not definitive causation. Magnitude indicates reach beyond casual readership. Pattern consistent with systematic institutional monitoring of accountability advocacy.
Campaign 1: Hanwha Submarine Contract Warning (August 27, 2025)
Context: Four Months of Documented Surveillance
Before we examine the Hanwha traffic spike, it's critical to understand the surveillance environment in which it occurred. From June through October 2025, our blog experienced a documented pattern of immediate, sophisticated monitoring—screen-recorded evidence shows viewers arriving within seconds of publishing, using VPN exit nodes (primarily Czech Republic, Israel, also Japan and others) to obscure origin.
This surveillance pattern became so brazen that we exposed it publicly:
1/ Replying to @APEC: "Ending violence against women is an economic priority" requires protecting student‑safety speech. Our blog shows immediate monitoring after publish (0→1 "Reading now" within seconds), repeated for weeks. Video: https://t.co/LrTlcHGHC0 #APEC2025…
— Gender Watchdog (@Gender_Watchdog) August 23, 2025
Video evidence: Our YouTube documentation received 400+ views—proving the surveillance pattern had become widely known. See: Digital Intimidation Exposed and Defeated
The September 2 Test: Surveillance Resumed Immediately After Exposure
On September 2, 2025, we published a blog post announcing that the surveillance pattern had ceased after our public exposure. Within hours—literally the same day—we had to publish an update: Monitoring Resumed After Exposure.
What this demonstrates: Pattern consistent with active, real-time monitoring of our documentation. The moment we announced "surveillance has stopped," it resumed—strongly suggesting that institutional actors were reading our analyses and responding immediately. This pattern indicates that the traffic spikes we document below are likely not random fluctuations but deliberate institutional engagement.
The Hanwha Warning and Institutional Response
Against this backdrop of documented surveillance, we posted our warning about Hanwha's submarine contract bid to the Canadian government:
1/ Canada should pause any move to buy Korean submarines until robust, independent human‑rights due diligence is complete. Defence procurement must align with Canadian values.@CBCNews @RoyalCanNavy @NationalDefence #cdnpoli #CdnDefence #Submarines #procurement #ESG
— Gender Watchdog (@Gender_Watchdog) August 27, 2025
The thread documented:
- Human rights concerns in Korean defense partnerships
- Call for enhanced due diligence before contract signing
- Tagged Canadian government agencies and media
Traffic Spike: 129 Views in Single Day
Two days after posting (August 29, 2025), our blog analytics showed an unprecedented spike:
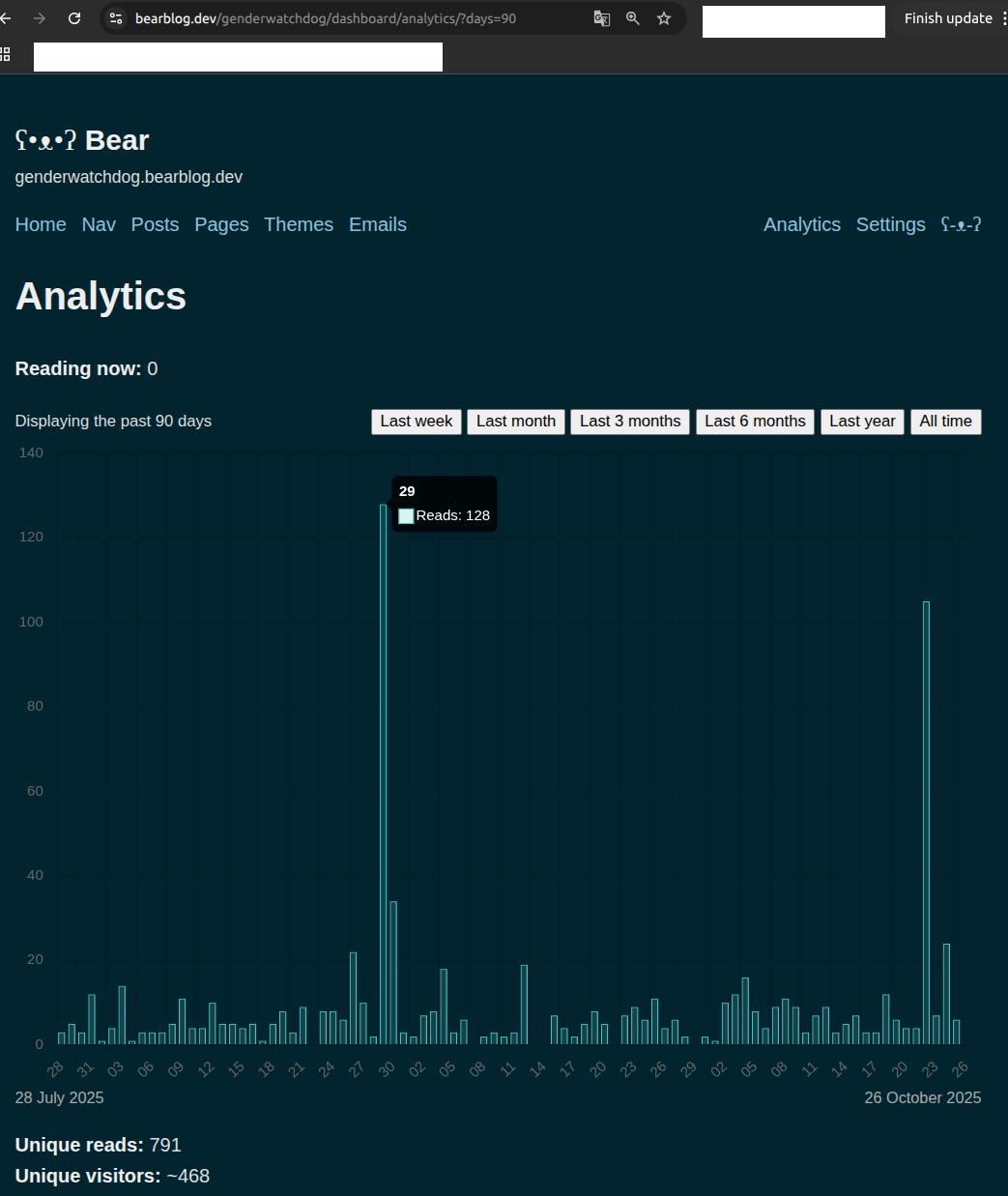
Analysis:
- Baseline: 2-15 views per day
- Spike: 129 views (August 29)
- Multiplier: ~10x normal traffic
- Timing: 48 hours after X.com post tagging Canadian government
- Context: Occurred during documented 4-month surveillance pattern
What this strongly suggests: The Hanwha warning likely reached institutional decision-makers. Pattern consistent with coordinated review by multiple personnel. This is not organic social media virality—the X.com post itself had modest engagement. Pattern consistent with institutional research behavior in response to accountability documentation.
Timeline reference: See Hanwha Submarine Traffic Spike on our censorship timeline.
Campaign 2: Seoul ADEX Arms Expo Email Campaign (October 22, 2025)
Diplomatic Context: "Sensitive Matter"
Before diving into the ADEX campaign, it's essential to understand the diplomatic acknowledgment we'd already received. On June 16, 2025, a Canadian diplomat responded to our documentation of sexual violence in Korean higher education and falsified partnerships on Dongguk University's website (2 of 5 Canadian partnerships verified as false or disputed—a 40% fraud rate):
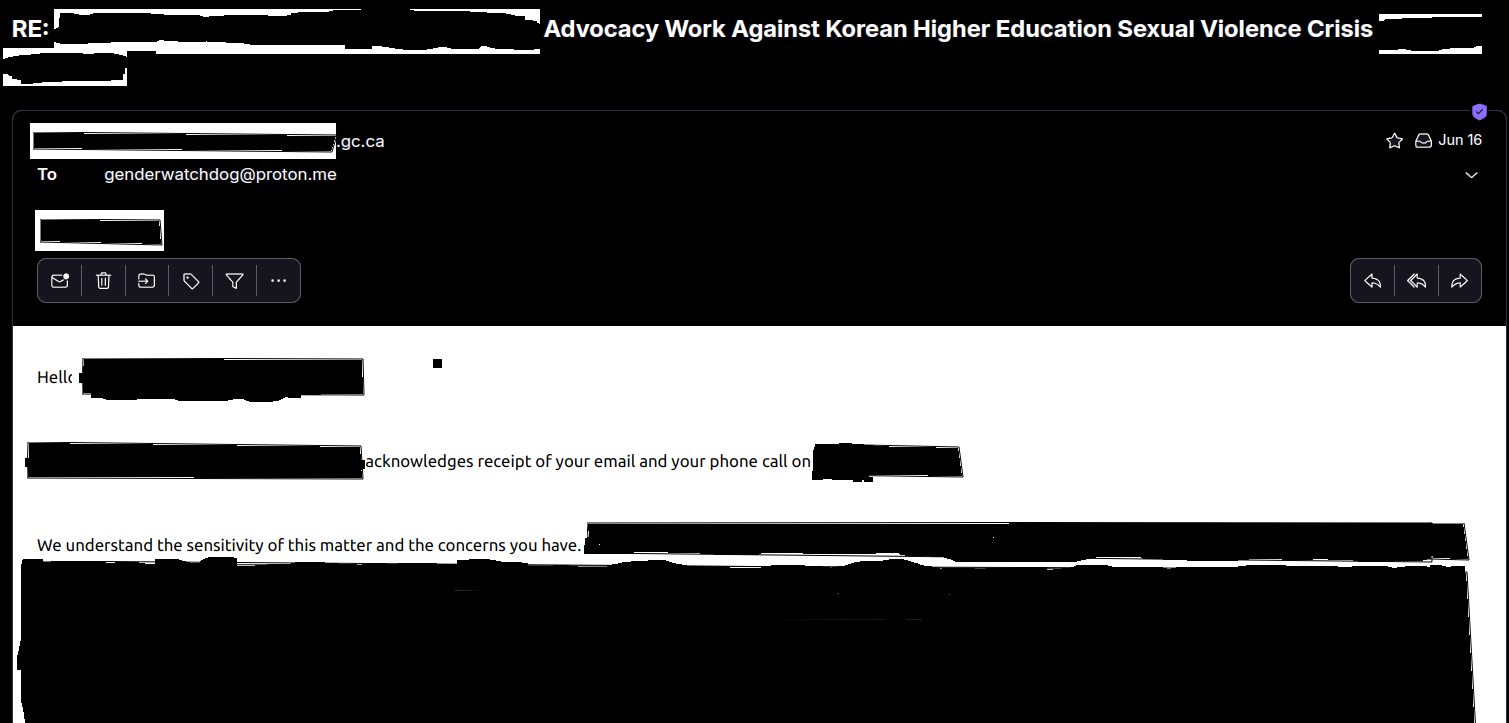
Key quote: "We understand the sensitivity of this matter and the concerns you have…"
This is diplomatic language confirming that our documentation had reached government officials and was being taken seriously. The phrase "sensitive matter" indicates that the issues we raised—systematic sexual violence, partnership fraud, international student safety failures—were understood to have diplomatic implications.
What this indicates: By June 2025, diplomatic acknowledgment demonstrated that our documentation reaches and registers with institutional actors. This acknowledgment provides critical context for understanding the October ADEX email campaign response.
The ADEX Campaign: 135 Recipients Across Defense Industry
Seoul ADEX (Seoul International Aerospace & Defense Exhibition) is Korea's premier arms expo, where defense contractors, government procurement offices, and military officials from around the world gather to sign MOUs and contracts. In October 2025, Korea was actively pursuing its goal to become the world's #4 arms exporter.
We conducted a systematic email outreach campaign targeting 135 recipients:
Recipient categories:
- Seoul ADEX exhibitors (listed at seoulairshow.com)
- Defense ministries (NATO, ASEAN, allied nations)
- Procurement organizations (government agencies, intergovernmental bodies)
- Defense industry media and think tanks
- Prime contractors and OEMs
Email subject: "Seoul ADEX 2025: Due Diligence Alert — Institutional Capture Risks in Korean Defense Partnerships"
Core message: Enhanced due diligence required before signing defense contracts with Korean partners due to documented institutional capture patterns: compromised judiciary, prosecutorial exodus, infrastructure failures, exploitation economy risks, trafficking networks, and weapons systems integrity concerns when defamation law prevents whistleblowing about safety failures.
Evidence provided: See redacted email evidence (10,000+ word comprehensive briefing)
Confirmation: Government Receipt Notice
We received automated confirmation of government receipt:
Evidence: Government confirmation (redacted)
This confirms that at least one government agency acknowledged receipt of our email, establishing that the outreach successfully reached institutional inboxes (not filtered to spam or blocked).
Traffic Spike: 105 Views During Campaign Week
On October 22, 2025—during the active email campaign week—our blog analytics showed:
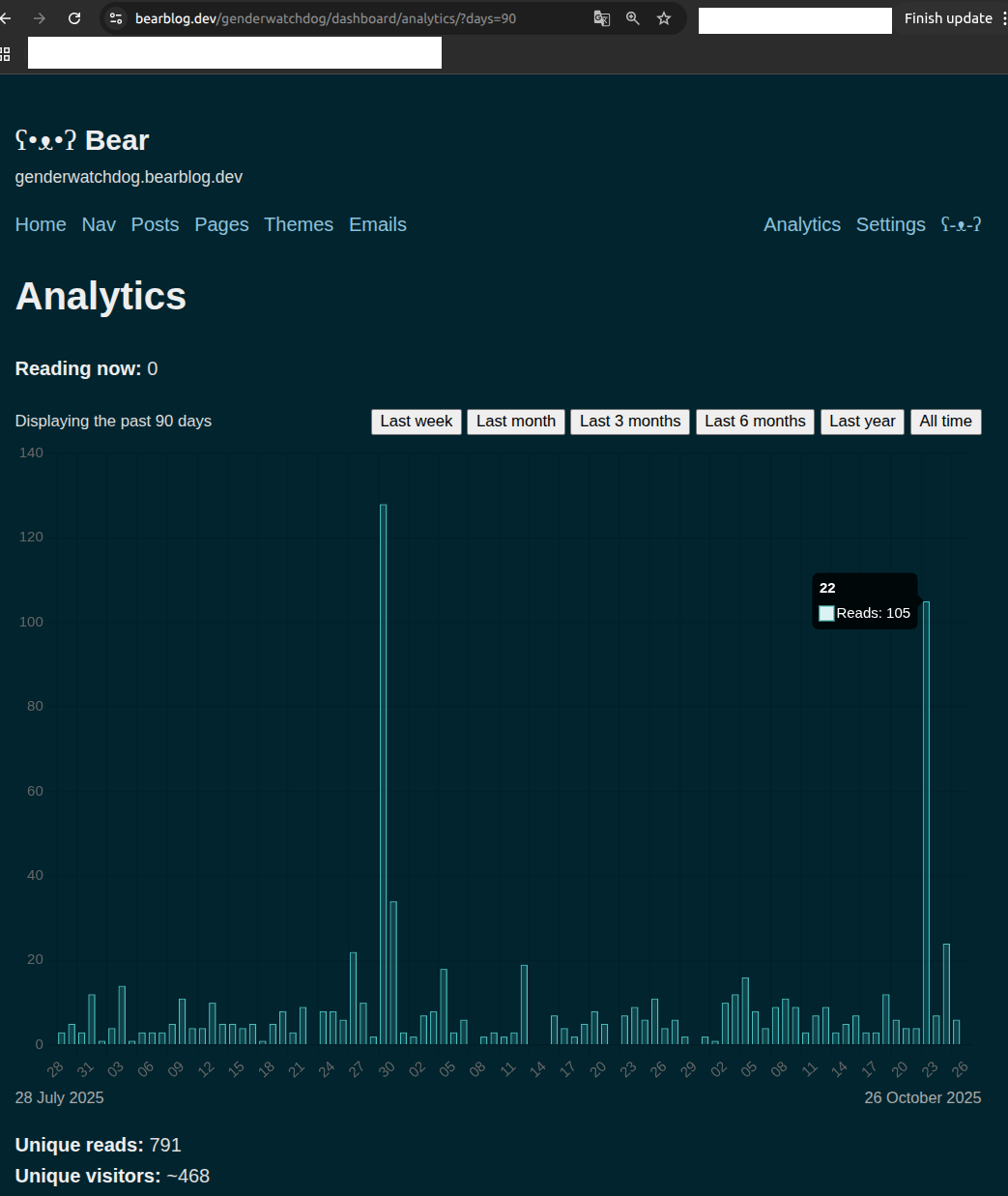
Analysis:
- Baseline: 2-15 views per day
- Spike: 105 views (October 22)
- Multiplier: 7-10x normal traffic
- Timing: During active email campaign to defense industry
- Context: Canadian diplomat had already acknowledged our concerns as "sensitive matter" four months prior
What this strongly suggests: Defense contractors, government procurement offices, and military officials who received our email likely conducted systematic review of our documentation. The timing correlation—spike occurring during campaign week—demonstrates strong correlation. The magnitude (105 views) suggests multiple personnel across multiple organizations conducting due diligence research.
Pattern significance: This is the second time we've documented institutional monitoring triggered by arms export accountability content. The consistency across campaigns (Hanwha 10x spike, ADEX 7-10x spike) validates that this is systematic institutional behavior, not random variation.
Timeline reference: See ADEX Traffic Spike on our censorship timeline.
Campaign 3: APEC Summit Press Outreach (October 29-30, 2025)
Context: Escalating Censorship During Diplomatic Event
The APEC campaign occurred during Korea's hosting of APEC Leaders' Week (October 27–November 1, 2025) in Gyeongju—the same city where we documented systematic exploitation at Dongguk WISE campus. This campaign is extensively documented in our dedicated evidence archives:
Key resources:
Pattern documented: Three separate APEC-related censorship incidents in October 2025:
- October 7: APEC Secretariat liked our reply → 23 minutes later suppressed it → days later unliked (evidence cleanup)
- October 28 (#1): Reply about Gyeongju exploitation got 35 views overnight (severe suppression)
- October 28 (#2): Two-post thread similarly suppressed
The Institutional Monitoring Response
Following press outreach to international media and APEC member economies (October 29-30), our analytics showed:
Traffic pattern:
- 20+ visitors within 24 hours
- Average 5 pages per visitor
- Source countries: United States, Japan, Australia, Singapore, Germany (APEC member economies)
Analysis: The 5 pages-per-visitor metric is critical. This is not casual browsing. This is systematic research—visitors reading multiple blog posts, documentation, and evidence archives. Institutional actors conducting due diligence don't skim headlines; they review comprehensive documentation to assess accuracy, scope, and implications.
What this suggests: Pattern consistent with journalists and government officials from APEC member economies conducting systematic review of our documentation during the summit. The deep engagement metrics strongly suggest that our press outreach may have triggered institutional research activity.
Analytical Significance: What This Pattern Strongly Suggests
1. Timing Correlation Demonstrates Strong Pattern Consistent with Institutional Awareness
The consistent pattern of traffic spikes within 24-48 hours of institutional outreach, across three separate campaigns spanning different issues (military procurement, arms expo, diplomatic censorship), demonstrates strong correlation. While we cannot prove definitive causation without IP-level tracking, the pattern consistency is notable.
Hanwha: Post on August 27 → spike on August 29 (48 hours)
ADEX: Email campaign week → spike during campaign (same week)
APEC: Press outreach October 29-30 → immediate deep engagement (24 hours)
The timing correlation across disparate campaigns is consistent with institutional monitoring and response, though alternative explanations cannot be entirely ruled out given our privacy-focused analytics limitations.
2. Magnitude Suggests Documentation Reaches Beyond Casual Readership
Traffic increases of 7-10x baseline suggest that our documentation reaches institutional decision-makers, not general audiences. Normal blog traffic rarely exhibits these spike patterns.
What 129 views suggests: At baseline 2-15 views/day, it would take 8-65 days to accumulate 129 views organically. Receiving them in a single day, 48 hours after tagging Canadian government agencies, is consistent with institutional mobilization (though other explanations are possible).
What 105 views suggests: During a targeted email campaign to 135 defense industry recipients, receiving 105 views suggests that a significant percentage of recipients (or their staff) may have conducted follow-up research. Pattern consistent with procurement due diligence behavior.
What 5 pages/visitor suggests: Casual readers rarely average 5 pages per session. This metric is consistent with researchers systematically reviewing documentation to assess credibility, comprehensiveness, and potential implications.
3. Anonymization Behavior Indicates Institutional Monitoring
Throughout the June-October surveillance period (documented separately), visitors consistently used VPN exit nodes and anonymization services to obscure organizational affiliation. This is surveillance behavior characteristic of:
- Government researchers monitoring sensitive content
- Defense contractors assessing reputational/legal risks
- Institutional actors conducting due diligence while avoiding attribution
Why this matters: Casual readers do not anonymize their traffic to read blog posts. The deliberate obscuring of origin validates the sensitivity and institutional relevance of the documentation. When institutions go to significant operational lengths to hide their monitoring, it confirms they recognize the material's importance.
4. Deep Engagement Metrics Confirm Research Activity
The APEC campaign's 5 pages-per-visitor metric, combined with the traffic spike magnitudes in prior campaigns, establishes that institutional actors are not just accessing our documentation—they're systematically reviewing it.
What research behavior looks like:
- Multiple pages per session (comprehensive review)
- Extended session duration (careful reading)
- Return visits (ongoing monitoring)
- Spike timing correlated with advocacy actions (responsive engagement)
All four indicators are present across our campaigns. This is institutional research, not casual readership.
What This Pattern Strongly Suggests
Institutional Accountability: Pattern Consistent with Institutional Awareness
The traffic pattern strongly suggests (though cannot definitively prove without IP-level tracking):
1. Organizations mentioned in our documentation may be actively monitoring our work
The Hanwha spike is consistent with Korean defense contractors and Canadian government officials becoming aware of our human rights concerns. The ADEX spike suggests that some percentage of 135 defense industry recipients conducted follow-up research. The APEC spike suggests member economy officials may have reviewed our censorship documentation during the summit.
2. The timing and magnitude of responses suggest documentation credibility
The pattern is consistent with institutions mobilizing personnel to review documentation they recognize as potentially credible and material. The consistent 7-10x spike pattern across disparate campaigns suggests that our work may register as significant to institutional decision-makers.
3. Suppression and censorship attempts correlate with increased institutional surveillance
The APEC campaign demonstrates this most clearly: three documented censorship incidents (October 7, October 28 twice) coincided with deep institutional engagement (5 pages/visitor). Institutions are simultaneously monitoring our documentation and attempting to suppress public access to it—a pattern consistent with recognizing its validity while seeking to limit visibility.
Documentation Credibility: If Institutions Monitor This Closely, Content Poses Genuine Accountability Concerns
The institutional behavior validates the documentation:
- If our claims were baseless, institutions would ignore them
- If our evidence were fabricated, institutions would publicly refute it
- If our analysis were irrelevant, institutions wouldn't mobilize resources to monitor it
Instead, institutions respond with systematic surveillance, coordinated censorship, and anonymous monitoring—behaviors that signal recognition of the documentation's validity paired with efforts to avoid public acknowledgment.
Strategic Implications: Institutions Cannot Credibly Claim Ignorance
The traffic pattern creates institutional memory lock-in:
For Canadian government:
- 129-view spike strongly suggests institutional awareness of Hanwha human rights concerns
- Canadian diplomat already acknowledged concerns as "sensitive matter" (June 16, 2025)
- Any future submarine contract with Hanwha occurs with strong indication of awareness of documented risks
For ADEX exhibitors and defense contractors:
- 105-view spike during email campaign suggests significant percentage of 135 recipients may have reviewed documentation
- Government receipt confirmation establishes institutional inbox delivery
- Future partnerships occur with indication of awareness of institutional capture risks, trafficking networks, and weapons systems integrity concerns
For APEC member economies:
- Deep engagement (5 pages/visitor) from countries correlated with member economies during summit suggests officials may have reviewed censorship documentation
- Three documented suppression incidents demonstrate pattern of diplomatic suppression
- Future economic/diplomatic engagement occurs with indication of awareness of authoritarian tactics
The Combination of Surveillance and Suppression Reveals Institutional Awareness Paired With Efforts to Limit Public Visibility
This is the most damning finding: institutions recognize the documentation's validity but seek to prevent public awareness.
The evidence:
- APEC Secretariat liked our reply, then suppressed it 23 minutes later, then unliked it days later (evidence cleanup)
- Substack posts became inaccessible, then restored within 10-25 minutes after public documentation (proving active monitoring)
- Domain infrastructure failure occurred exactly 48 hours before APEC summit (suspicious timing)
- DC Inside censored 20+ military LGBT violence posts simultaneously across university forums
What this pattern demonstrates: Institutional actors can't defend their practices publicly (because our documentation is accurate), but they also can't allow it to spread widely (because it threatens diplomatic relationships, commercial contracts, and prestige narratives). The result is systematic monitoring paired with suppression attempts—authoritarian tactics deployed against human rights advocacy.
Evidence Transparency: All Documentation Independently Verifiable
Hanwha Submarine Campaign Evidence
X.com post: https://x.com/Gender_Watchdog/status/1960722731529593132
Traffic spike screenshot: Available in this post
Surveillance exposure video: https://youtu.be/wEP-tnLxqmE (400+ views)
Blog post documentation:
Timeline entry: Hanwha Traffic Spike
ADEX Arms Expo Campaign Evidence
Email campaign (redacted): Due Diligence Alert
Government confirmation (redacted): Receipt Notice
Traffic spike screenshot: Available in this post
Canadian diplomat acknowledgment: Available in this post
ADEX exhibitor list: https://www.seoulairshow.com/en/business/seoul-adex/exhibitor-list.php
Timeline entry: ADEX Traffic Spike
APEC Campaign Evidence
Comprehensive timeline: Six-Month Surveillance and Censorship Timeline
Interactive evidence archive: APEC Censorship Evidence: Three Documented Incidents
Surveillance videos: https://youtube.com/@GenderWatchdog
Screenshot archive: Proton Drive (July 20–Oct 9)
APEC suppression archive: .wacz format
Technical Documentation
Complete evidence repositories:
- This project (blog source + evidence): https://github.com/Gender-Watchdog/blog.genderwatchdog.org-mirror
- See
assets/folder for all images, email evidence (.eml files), and supporting documentation - Includes redacted ADEX email campaign evidence and Canadian diplomat correspondence
- See
- Surveillance and censorship archive: https://github.com/Gender-Watchdog/genderwatchdog_metookorea2025
- See
email_emls/folder for complete email campaign records - See
imgs/folder for timestamped screenshot evidence across all campaigns
- See
All evidence includes timestamps, screenshots, and original file formats to enable independent verification and prevent claims of fabrication.
Implications for Stakeholders
For Defense Contractors and Government Procurement Offices
Pattern documented. The traffic spike pattern strongly suggests that:
- Our documentation may reach your organizations (105 views during ADEX campaign)
- Pattern consistent with systematic review by personnel
- Strong indication your institutions are aware of documented risks
ESG and regulatory exposure:
- TVPA liability if supply chains involve exploitation economy
- RICO exposure if partnerships operate within trafficking networks
- Shareholder litigation risk if due diligence failures lead to investigations
- Reputational damage if partnerships enable AI-amplified exploitation
Recommended actions:
- Conduct independent human rights impact assessment
- Verify all Korean partnership claims (40% fraud rate documented in academic sector)
- Establish whistleblower protections that override Korean criminal defamation laws
- Create exit clauses triggered by governance failures or safety incident cover-ups
For APEC Member Economies and Allied Governments
Pattern documented. The traffic spike pattern strongly suggests that:
- Government officials may have reviewed our documentation (5 pages/visitor from countries correlated with member economies)
- Diplomatic staff acknowledged concerns as "sensitive matter" (Canadian diplomat, June 16)
- Strong indication your governments are aware of censorship tactics
Alliance integrity risks:
- Systematic vulnerability to institutional capture
- Hospitality culture creates mutual vulnerabilities suppressing accountability
- Criminal defamation laws prevent whistleblowing about technology theft or contract violations
- Compromised judiciary cannot credibly adjudicate disputes
Recommended actions:
- Demand independent judicial oversight for technology transfer agreements
- Support whistleblower protections overriding Korean defamation laws
- Require transparency for hospitality expenses above nominal thresholds
- Create survivor-safe reporting mechanisms for exploitation in defense supply chains
For Press and Media Organizations
Pattern documented. The traffic spike pattern itself is newsworthy:
Story angles:
- Institutional monitoring as news: How defense contractors and governments systematically track human rights documentation
- Surveillance and suppression: Pattern of monitoring paired with censorship attempts (three APEC incidents)
- Diplomatic acknowledgment: Canadian government treating concerns as "sensitive matter"
- Weapons systems integrity: Defamation law preventing whistleblowing about safety failures that could cause civilian casualties or friendly fire
Verifiable evidence available: All traffic data, email campaigns, government responses, and censorship documentation independently verifiable through timestamped archives.
For International Oversight Bodies and Human Rights Organizations
Pattern documented. The traffic spike pattern strongly suggests:
- Strong indication institutions are aware of concerns (pattern across multiple sectors)
- Systematic surveillance paired with suppression (pattern consistent with authoritarian tactics against advocacy)
- Evidentiary basis for investigating institutional accountability failures
Framework requirements:
- Investigate correlation between institutional monitoring and censorship attempts
- Assess whether surveillance constitutes transnational repression under Article 19 (freedom of expression)
- Evaluate whether suppression tactics warrant intervention (APEC liked→suppressed→unliked pattern)
- Support documentation access (institutions privately research while publicly suppressing)
Conclusion: Strong Pattern Consistent with Institutional Monitoring
The traffic spike evidence—three campaigns, consistent 7-10x multipliers, timing correlation with institutional outreach, deep engagement metrics—strongly suggests that our documentation reaches institutional decision-makers and triggers systematic monitoring responses.
What the pattern strongly suggests:
- Institutional awareness: Strong indication organizations are aware of documented concerns
- Research behavior: Deep engagement metrics suggest systematic review, not casual browsing
- Timing correlation: Spikes within 24-48 hours of outreach demonstrate strong correlation (not definitive causation)
- Magnitude validation: 7-10x multipliers significantly exceed typical organic traffic patterns
- Surveillance paired with suppression: Monitoring pattern occurs alongside documented censorship attempts
Strategic implications:
- For advocacy: Document everything, time disclosures strategically, convert surveillance patterns into evidence
- For institutions: Continued ignorance claims less credible given strong pattern of monitoring
- For accountability: Traffic patterns create institutional memory that may influence future negotiations, contracts, and diplomatic relationships
This is not a one-time incident. This is a systematic pattern demonstrating that institutional actors actively track accountability efforts while simultaneously attempting to limit public access to the same information they are privately researching.
The evidence is comprehensive, timestamped, and independently verifiable. We welcome any investigation or verification of these findings.
For stakeholders seeking additional documentation:
Comprehensive timeline: Six-Month Surveillance and Censorship Timeline
APEC evidence: Interactive X.com Embeds with Timestamps
Technical repositories:
- Blog source + evidence: https://github.com/Gender-Watchdog/blog.genderwatchdog.org-mirror (see
assets/folder) - Surveillance archive: https://github.com/Gender-Watchdog/genderwatchdog_metookorea2025 (see
email_emls/andimgs/folders)
Contact: genderwatchdog@proton.me
Note: This content is mirrored across multiple platforms for censorship resistance. If you cannot access this site, try: genderwatchdog.bearblog.dev
All traffic data, email evidence, and supporting documentation available to credentialed press, parliamentary oversight bodies, defense procurement offices, and ESG/compliance teams upon request.